APPLICATION EXAMPLES
Protecting safety-critical applications from network hacking, password hacking and other cyber-attack techniques
At duagon, our customers have the advantage of having everything they need for their secure application supplied by a single supplier. By having secure hardware products and software features all under one roof, our customers have one single point of contact working with them from the very beginning of their project through to continued support once the system is running.
ENHANCED MEDIA CONVERSION GATEWAYS
Our proven gateway product range for media and protocol translation has been enhanced with cyber security features to be the best fit for your next train project and offers secure configuration and diagnostics.
Flexible Protocol Translation
- Versatile media converters to either connect a legacy bus (CAN/RS/MVB) component to the ECN or an Ethernet device to MVB/CAN/RS.
- Support for ethernet redundancy handling (dual homing)
- Standard mapping applications without the need to write a custom application
- Possibility for advanced mapping and services implementation based on customer requirements by our application engineering team or using our development library supporting process and message data.
Secure Maintenance
- Role based user access with remote authentication services (e.g. Radius client)
- SW integrity checks and secure, certificate based, firmware update procedures
- Encrypted communication to our web services via sftp/ssh/https
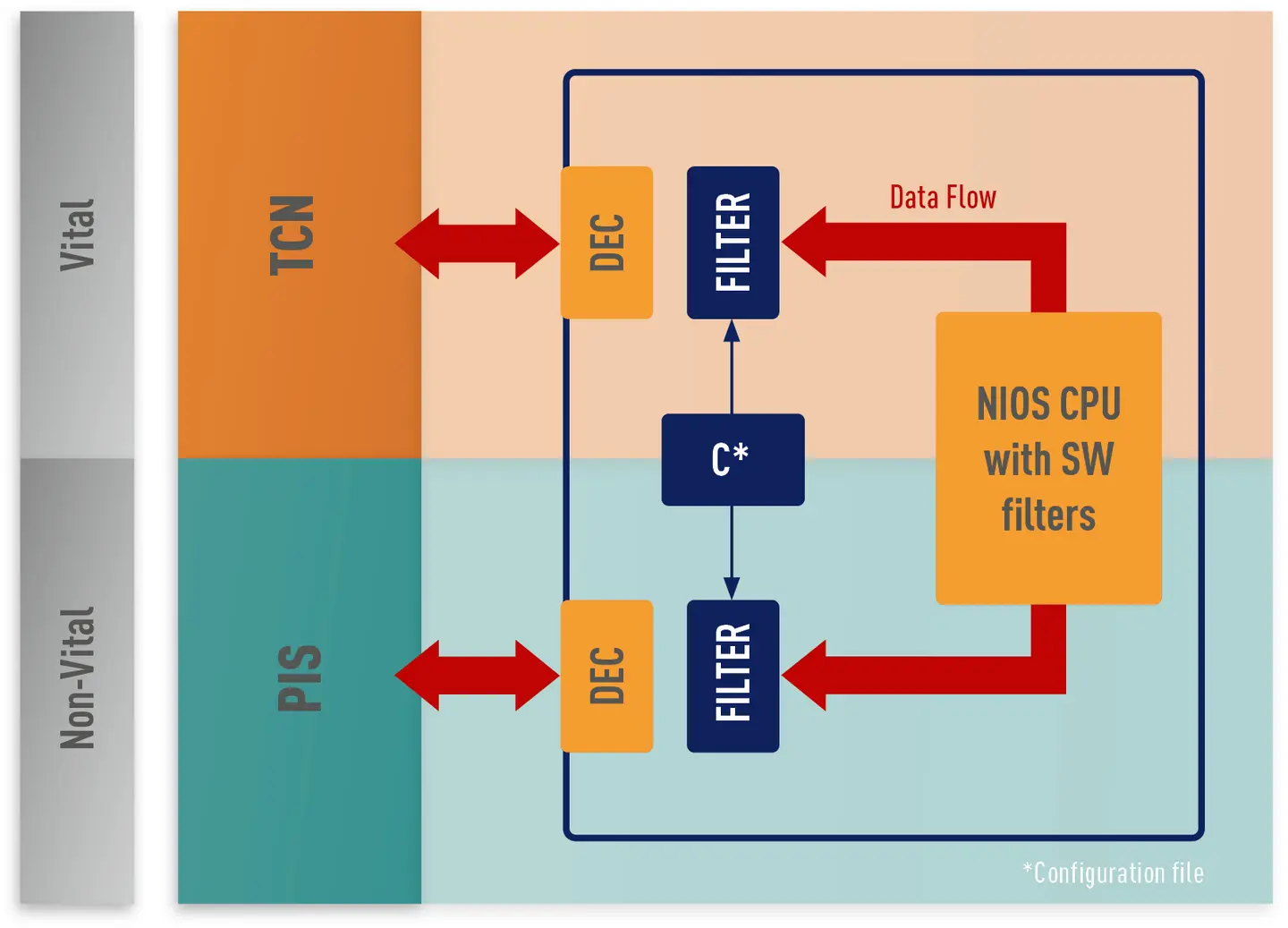
CONFIGURABLE HARDWARE & SOFTWARE FILTERS
Network separation through fixed static or dynamic IP packet filtering.
Hard coded hardware filters
- Directly implemented in the FPGA with no influence on the speed of data flow
- Can be configured with a configuration file, e.g. a text file, to allow greater flexibility. Possibility of locking the memory once the configuration file has been loaded
NIOS softcore filtering CPU
- CPU implemented in the FPGA, solely dedicated to package filtering
- Minimal influence on the package throughput
- Can be user-programmed in C
Properties
- Static, configurable filtering
- Dynamic filtering in dedicated CPU
- Up to 100 static filters, dynamic filter up to memory capacity
DIN-Rail Computing Platform
The MC50M is the ideal basis for functions such as security gateway, wireless IoT gateway, predictive maintenance, ticketing system, or to act as a diagnostics server. This DIN-rail mountable module comes with three physically separate Ethernet ports. A secured vital network may be connected to the first port, an unsecured network (internet) to the second while the third port may be used for maintenance. In this use case the MC50M protects the vital train infrastructure from malicious traffic, viruses and malware. The MC50M may be extended with Serial Ports, an MVB or CAN bus interface or wireless communication interfaces such as LTE and WLAN.
Features:
- 3 Separate Ethernet ports with three MAC addresses - supporting cyber security applications
- Intel Atom E3900 series
- Up to 8 GB DDR3 RAM with ECC
- Trusted Platform Module
- M.2 NVMe slot for storage
- Gb Ethernet, USB 3.2 Gen 1x1, RS232, RS485/422, DisplayPort
- DIN-Rail, wall or 19" rack mounting
- Input voltage 24 V DC nom. or 48 V DC nom. with ignition
- Full range power supply 16 V DC to 60 V DC
- EN 50155 compliant (railways)
- -40 °C to +70 °C (+85 °C), fanless
SECURE WAKE-UP FUNCTION
Secure web front-end (HTTPS), that can be used for diagnostic purposes and to upload and execute firmware updates.
Secure ETH connection (ssh)
> Receiving wake-up trigger
< Confirm wake-up state
Secure communication protocols like HTTPS web server, SFTP file transfer, SSH CLI
- Authentication by password, public key or host based
- 2x digital outputs (24-110V); bi-directional solid state relay output with current limitation
- 2x digital inputs (24-110V); state, PWM or frequency input
- 2x2 analog inputs; voltage, current, resistance
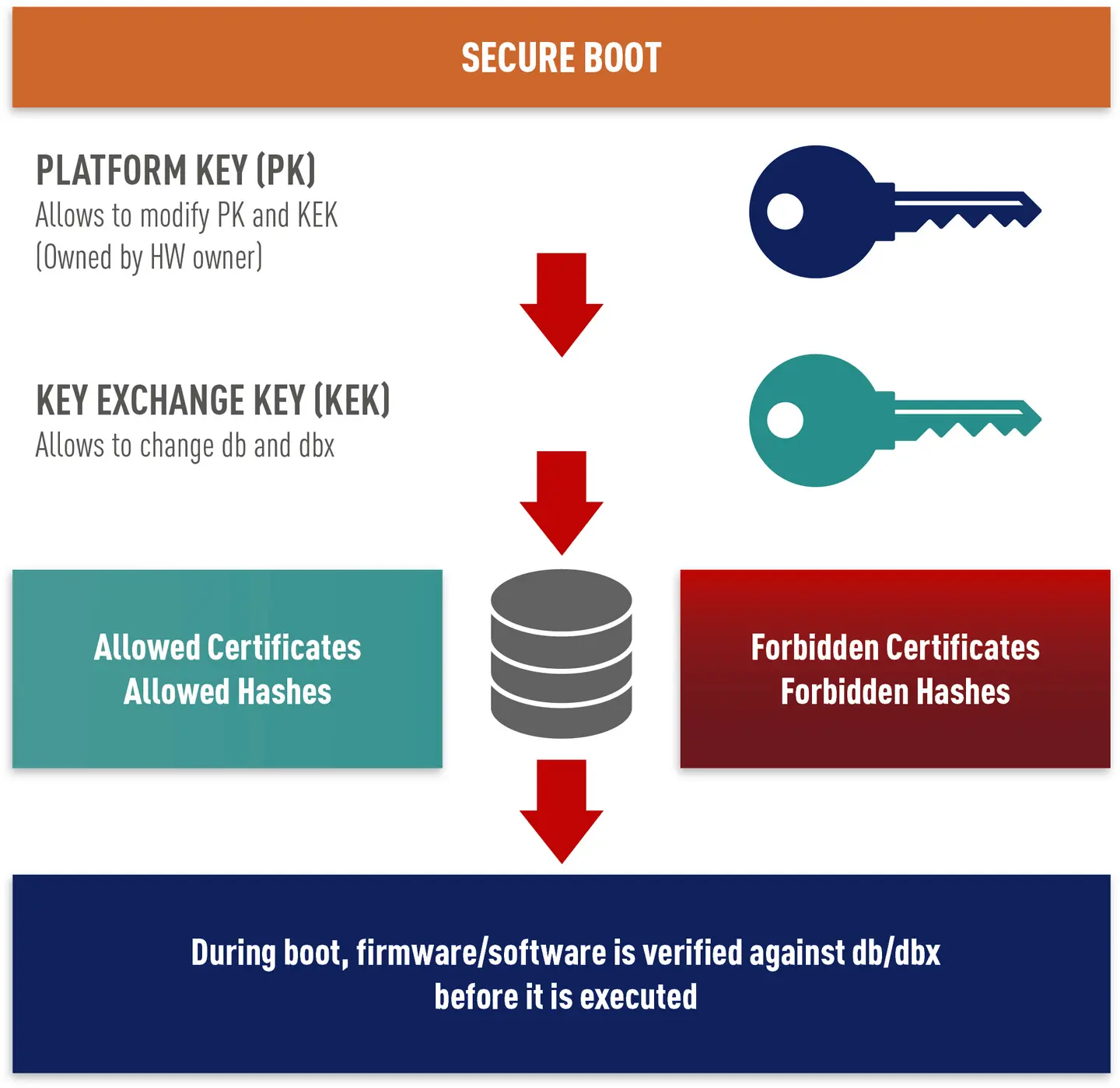
SECURE BOOT – SOFTWARE INTEGRITY CHECK
- A private key is used to create a signature of each software package (OS, drivers, application)
- With the corresponding public key, the authenticity of the software is checked before it is booted or executed
- Keyhandling methods enable customer to make use of an own set of keys, independent from keys created by manufacturer (platform key, key exchange key)
PRODUCTS:
Contact Support & Sales
Do you need to protect your system from cyberattacks?
Our international team of engineers and sales consultants are here to help - no matter where in the world you are.
At duagon we have a wide range of standard products ready for use, and our products can be customized for use in a specific application environment. Our sales team is here to provide more specific information about our standard hardware range, our software technology, the required standards and certifications, and, together with our team of engineers, developing the optimal solution to your specific application requirements.